Publicly Available In-House Developed Hardware Security Software/Tools and New HLS Benchmarks for the Research Community (also available in IEEE CEDA 'CAD for Assurance')
Download Section (Free Publicly available):- In-House Developed Hardware Security Software/Tools and New HLS Benchmarks for the Research Community (also available in IEEE CEDA 'CAD for Assurance')
Click here for accessing/downloading the "new HLS benchmarks" details including the CDFG, Datapath etc.
The document above provides details of several new HLS benchmarks that have been employed in the hardware security area. More explicitly, the new HLS benchmarks have been employed in HLS security research by
the authors. The document provides a complete benchmark guideline of these new applications from the domain of machine learning, multimedia, medical systems, signal processing etc, starting from the transfer function, CDFG and
its HLS datapath design. The document provides a one-stop reference for researchers working on HLS security which will help them in advancing the research field.
Click here for accessing the readme file - "How to create the input application file format for all the tools": Sample demonstration given for 8-point DCT application
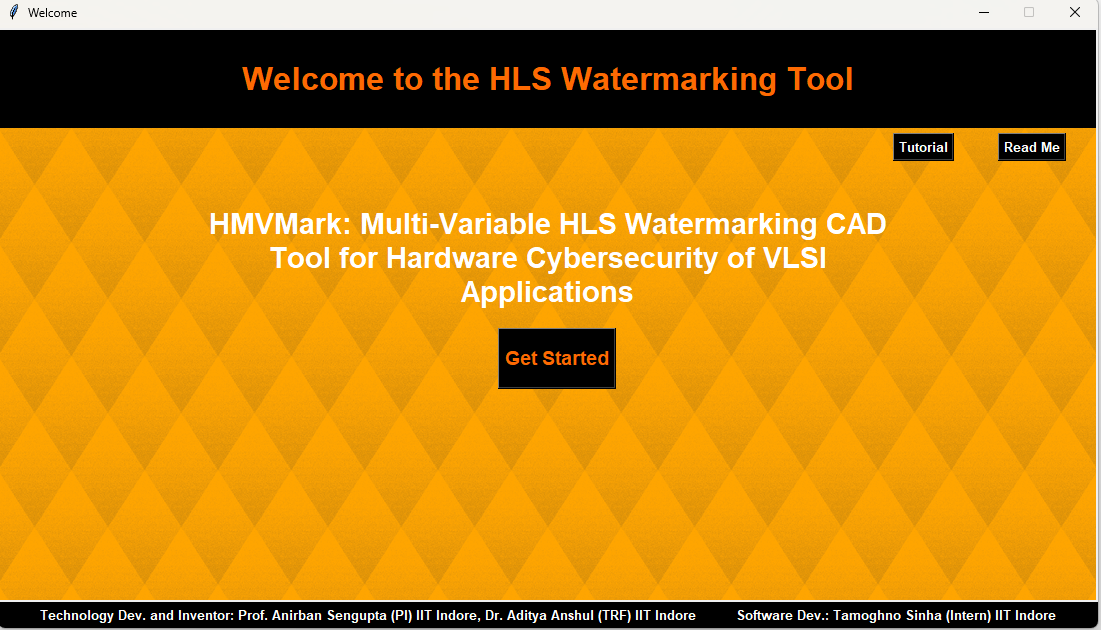
(1) HMVMark: Multi-Variable HLS Watermarking CAD Tool for Hardware Cybersecurity of VLSI Applications
Click here for tool download
Click here to view the high-resolution tool GUI image
Summary, Threat Model and Objective: Prof. Anirban Sengupta and his team have developed a multi-variable signature based hardware security/watermarking computer aided design (CAD) tool to generate secure intellectual property (IP) design for data intensive very large scale integration (VLSI) applications, which provides detective control against IP piracy and false claim of ownership threats. The tool is capable of generating a unique IP vendor’s/designer’s multi-variable watermark signature, further embedded in IP design during high-level synthesis process. The objective is to provide robust detection against IP piracy and false IP ownership claim by an adversary in the system-on-chip (SoC) integrator house.
Details of the tool : The top half of the tool (Input Panel) shows the panel for providing the required inputs to the tool. The HMVMark tool requires the data intensive application’s CDFG text file, library file, adder and multiplier constraints as well as the watermark signature as input from the user for generating hardware watermark constraints. The tool shows all the intermediate steps of the approach to generate secure IP data path design with embedded multi-variable watermark signature, including the design latency, area and the obtained cost function for the user’s configuration. Further, it shows scheduled data flow graph (SDFG), pre and post watermark embedding coloured interval graphs (CIG) and the register allocation table (RAT) pre and post embedding the watermark signature constraints (watermarking) at the output panel. Finally, the tool provides a detailed RTL information Table via the output panel depicting the number of registers, storage variables, operators, latches, muxes and demuxes used in the post watermarking design. The generated IP design contains the IP vendor’s robust digital evidence (in terms of multi-variable watermark signature) that provides detective countermeasure against IP piracy and false IP ownership claim.
Click here for accessing The tutorial file of the tool
Supporting IEEE Publications:
A. Sengupta and S. Bhadauria, "Exploring Low Cost Optimal Watermark for Reusable IP Cores During High Level Synthesis," in IEEE Access, vol. 4, pp. 2198-2215, 2016 DOI: 10.1109/ACCESS.2016.255205
(2) HarDMark: CAD based DNA Fingerprint as Watermark Countermeasure for
Hardware Cybersecurity of VLSI Applications
Click here for tool download
Click here to view the high-resolution tool GUI image
Summary, Threat Model, and Objective : Prof. Anirban Sengupta and his team have developed a DNA Fingerprint Profiling based hardware security/watermarking computer aided design (CAD) tool to generate secure intellectual property (IP) design for data intensive very large scale integration (VLSI) applications, which provides detective control against IP piracy and false claim of ownership threats. The tool is capable of generating a unique IP vendor’s/designer’s DNA Fingerprint watermark signature, further embedded in IP design during the high-level synthesis process. The objective is to provide robust detection against IP piracy and false IP ownership claim by an adversary in the system-on-chip (SoC) integrator house.
Details of the tool : The left portion of the tool (Input Panel) shows the panel for providing required inputs to the tool, the right portion comprises two different panels, viz. Output Panel and Status Panel. The output panel contains output buttons to see the intermediate and final outputs of the DNA fingerprint watermarking CAD tool. The status panel shows the status of the intermediate steps (i.e., generating scheduled design, generating DNA fragments, DNA fragment replication, final DNA signature sequence generation, generating AES encrypted signature and generating watermark security constraints) in generating hardware security/watermarking constraints from the IP vendor’s DNA sequence and AES key. Initially, the output panel and status panel buttons/bars remain yellow and red. Upon applying the inputs, the respective status buttons turn blue. The DNA fingerprint watermarking CAD tool accepts the following inputs: data intensive application input in the form control dataflow graph (CDFG) along with the designer specified resource constraints (i.e., #adders, #multipliers, etc.), IP vendor’s DNA sequence and restrictions enzymes (REs), AES key, and encoding rules for generating hardware watermark constraints. The tool shows all the intermediate steps of the approach to generate a secure IP data path design with an embedded encrypted DNA fingerprint signature. Further, it shows scheduled design, DNA fragments post applying RE-1 and RE-2, replicated DNA fragments, final DNA signature sequence, the generated final encrypted DNA fingerprint signature and corresponding hardware security/watermark constraints at the output panel. Furthermore, it also shows the registers allocation pre and post embedding DNA fingerprint signature constraints (watermarking), watermark design area, watermark design latency and watermark design cost at the output panel. The post-watermark register allocation table is further synthesized into its corresponding secure register transfer level (RTL) datapath and controller design. The generated IP design contains robust IP vendor’s digital evidence (in terms of DNA fingerprint watermark signature) that provides detective countermeasure against IP piracy and false IP ownership claim.
Click here for accessing The tutorial file of the tool
Supporting IEEE Publications:
1) A. Sengupta, N. Bhui, A. Anshul, et al. Bio-mimicking DNA fingerprint profiling for HLS watermarking to counter hardware IP piracy. Nature Sci Rep 14, 22413 (2024). https://doi.org/10.1038/s41598-024-73119-y
2) A. Sengupta, N. Bhui and A. Anshul, "High Level Synthesis Based Forensic Watermarking of Hardware IPs using IP Vendor’s DNA Signature," in IEEE Embedded Systems Letters, doi: 10.1109/LES.2025.3566674.
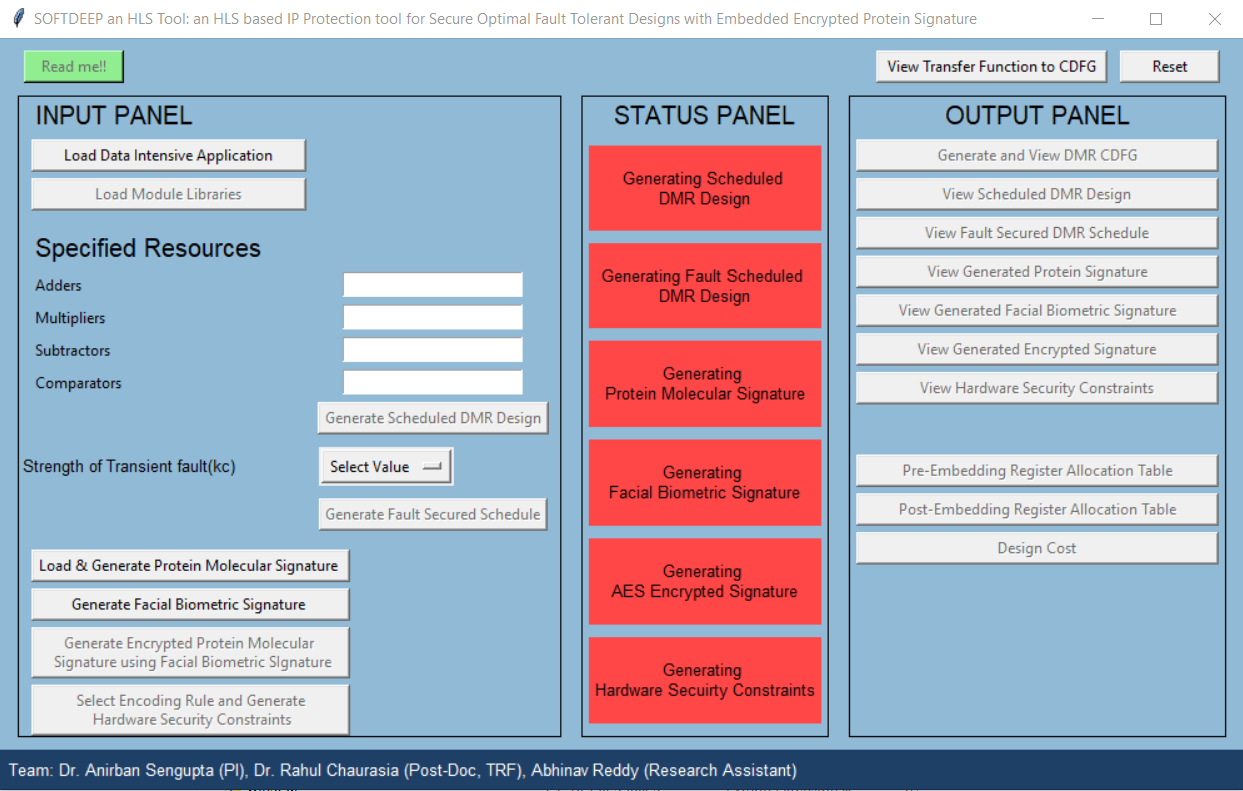
(3) SOFTDEEP : an HLS based IP Protection tool for Secure Optimal Fault Tolerant Designs with Embedded Encrypted Protein signature
Click here for tool download
Click here to access the tool/Software in IEEE CEDA 'CAD for Assurance'
Click here to view the high-resolution tool GUI image
Summary and Threat Model :Dr. Anirban Sengupta and his team have developed a
Molecular biometric based hardware security tool to simulate and analyse the design
space exploration method producing secure design solutions for data intensive
application frameworks with ability of k-cycle transient fault detection and/or error
correction and detective control against piracy and false claim of ownership threats
and generation of an optimal k-cycle transient fault detectable and /or fault correctable
datapath processors with embedded protein biometric signature sample of an
intellectual property (IP) vendor during high-level synthesis of integrated circuits (ICs).
Objective of the tool :The left portion of the tool shows the panel for providing required
inputs to the tool, right portion shows the panel with output buttons to see the
intermediate and final outputs of the protein biometric based hardware security
approach. The panel in the middle shows the status of the intermediate steps (i.e.
generating scheduled dual modular redundant (DMR) design, generating fault
scheduled DMR design, generating protein molecular signature, generating facial
biometric signature, generating ‘AES’ encrypted signature and generating hardware
security constraints) in generating hardware security constraints from IP vendor’s
protein molecular signature (input) encrypted using facial biometric signature based
encryption key. Initially, these status bars remain Red. Upon applying the inputs, the
respective status bar turns Green. The Molecular biometric based hardware security
tool accepts the following inputs: data intensive application input in the form control
dataflow graph (CDFG) along with the designer specified resource constraints,
transient fault strength, protein molecular sequence and captured facial biometric
image of the IP vendor for generating encrypted protein molecular signature using
facial biometric encryption key, and IP vendor specified encoding algorithm for
generating hardware security constraints. The tool shows all the intermediate steps of
the approach to generate secure optimal K-cycle fault tolerant data path processor with
embedded encrypted protein molecular biometric. Further, it shows scheduled DMR
design, fault secured DMR schedule, protein molecular signature, facial biometric
signature and the finally generated encrypted protein molecular signature and
corresponding hardware security constraints at the output. Furthermore, it also shows
the registers allocation pre and post embedding protein molecular signature
constraints, design area, latency and cost onto the output window. The employed
security against transient fault ensures the reliable functionality and the embedded
protein molecular signature in the fault secured datapath processor design act as
unique digital evidence to secure against piracy and false claim of ownership threats.
Click here for accessing The tutorial file of the tool
Click here for accessing The database required for facial image input
Supporting IEEE Publications:
A. Sengupta, R. Chaurasia and A. Anshul, "Robust Security of Hardware Accelerators Using
Protein Molecular Biometric Signature and Facial Biometric Encryption Key," IEEE
Transactions on Very Large Scale Integration (VLSI) Systems, vol. 31, no. 6, pp. 826-839,
June 2023, doi: 10.1109/TVLSI.2023.3265559.
A. Sengupta and M. Rathor, "Facial Biometric for Securing Hardware Accelerators," IEEE
Transactions on Very Large Scale Integration (VLSI) Systems, vol. 29, no. 1, pp. 112-123,
Jan. 2021, doi: 10.1109/TVLSI.2020.3029245.
A. Sengupta, R. Chaurasia, A. Anshul, "Hardware Security of Digital Image Filter IP Cores against Piracy using IP Seller’s Fingerprint Encrypted Amino Acid Biometric Sample", Proceedings of 8th IEEE Asian Hardware Oriented Security and Trust Symposium (AsianHOST) , China, Accepted, 2023.
Anirban Sengupta "Design Space Exploration of Optimal k-Cycle Transient Fault Tolerant
Datapath Based on Multi-Objective Power-Performance Tradeoff", Patent No. 392356, 2022,
Granted by Indian Patent Office (IPO), Govt. of India.
(4) Faciometric Hardware Security Tool
Click here to access the tool/Software in IEEE CEDA 'CAD for Assurance'
Click here for tool download
Click here to view the high-resolution tool GUI image
Summary and Threat Model :Dr. Sengupta and his team have developed a Faciometric hardware security tool to simulate and analyse the functionality of facial biometric based approach for securing DSP hardware accelerators against piracy and false claim of ownership threats.
Objective of the toolThe left portion of the tool shows the panel for providing required inputs to the tool, right portion shows the panel with output buttons to see the intermediate and final outputs of the facial biometric based hardware security approach. The panel in the middle shows the status of the intermediate steps (i.e. capture facial biometric with required grid size, generate nodal points and facial features set, calculation of feature dimensions for selected features, facial signature generation and conversion to hardware security constraints) in generating hardware security constraints from a captured/input facial image. Initially, these status bars remain Red. Upon applying the inputs, the respective status bar turns Green. The Faciometric hardware security tool accepts the DSP application input in the form CDFG along with the resource constraints. The tool shows all the intermediate steps of facial biometric based hardware security approach and the finally generated facial signature and corresponding hardware security constraints at the output. Further, it also shows scheduling and registers allocation pre and post embedding facial signature constraints, onto the output window. The embedded facial signature in the hardware accelerator design can be used as a unique digital evidence to secure against piracy and false claim of ownership threats.
Click here for accessing The video tutorial of the tool
Click here for accessing The database required for facial image input
Supporting IEEE Publications:
A. Sengupta and M. Rathor, "Facial Biometric for Securing Hardware Accelerators," in IEEE Transactions on Very Large Scale Integration (VLSI) Systems, vol. 29, no. 1, pp. 112-123, Jan. 2021, doi: 10.1109/TVLSI.2020.3029245
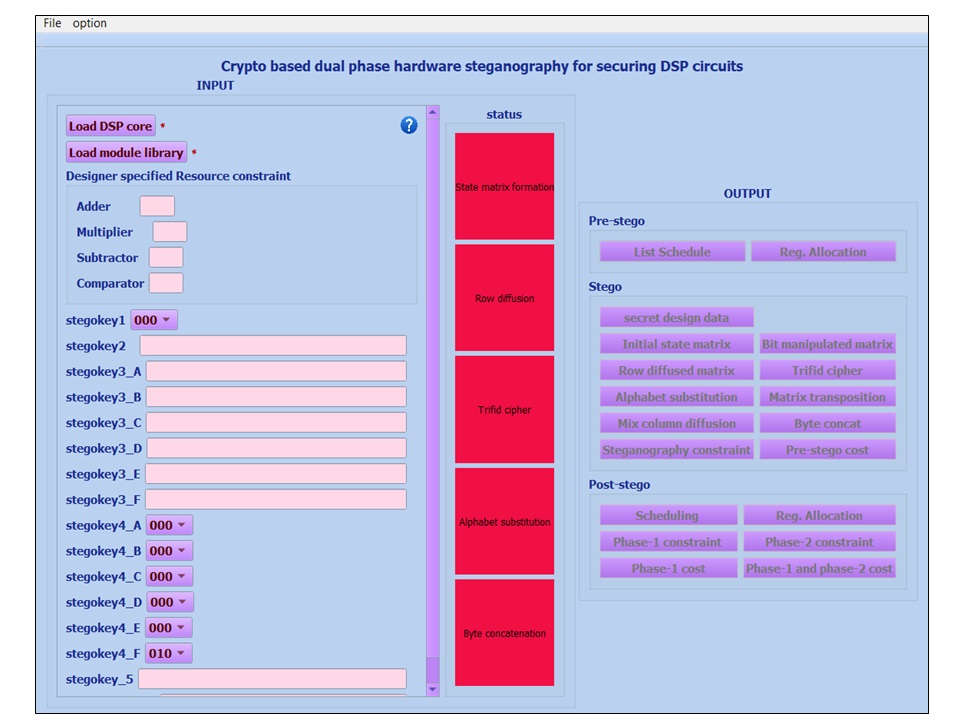
(5) Crypto-stego tool
-: Crypto-steganography tool
Click here to access the tool/Software in IEEE CEDA 'CAD for Assurance'
Click here for tool download
Click here to view the high-resolution tool GUI image
Summary and Threat Model : Dr. Sengupta and his team have developed a Crypto-Stego tool to simulate and analyse the functionality of crypto-based steganography approach for securing DSP hardware accelerators against piracy and false claim of ownership threats.
Objective of the tool: The left portion of the tool shows the panel for providing required inputs to the tool, right portion shows the panel with output buttons to see the intermediate and final outputs of the crypto-based steganography approach. The panel in the middle shows the status of the key-driven steps (i.e. state matrix formation, row diffusion, Trifid cipher, alphabet substitution and byte concatenation) of the crypto-based steganography approach. Initially, these status bars remain Red. Upon applying the stego-key, the respective status bar turns Blue. The Crypto-Stego tool accepts the DSP application input in the form CDFG along with module library and resource constraints. The tool shows all the intermediate steps of crypto-based steganography and the finally generated stego-constraints at the output. Further, it also shows scheduling and registers allocation pre and post embedded steganography constraints, onto the output window. The embedded steganography constraints in the hardware accelerator design can be used as digital evidence to secure against piracy and false claim of ownership threats.
Click here for accessing chapter 2 of the IET book on "Secured hardware accelerators for DSP and image processing applications" where details of the tool are provided
Supporting IEEE Publications:
- Anirban Sengupta, Mahendra Rathor "IP Core Steganography for Protecting DSP Kernels used in CE Systems", IEEE Transactions on Consumer Electronics (TCE) , Volume: 65 , Issue: 4 , Nov. 2019, pp. 506 - 515
- Anirban Sengupta, Mahendra Rathor "Structural Obfuscation and Crypto-Steganography based Secured JPEG Compression Hardware for Medical Imaging Systems", IEEE Access, Volume: 8, Issue:1, Dec 2020, pp. 6543-6565
- Mahendra Rathor, Anirban Sengupta "Design Flow of Secured N-point DFT Application Specific Processor using Obfuscation and Steganography", IEEE Letters of the Computer Society (LOCS) , Volume: 3 , Issue: 1 , June 2020, pp. 13 - 16.
- Anirban Sengupta, Mahendra Rathor "Crypto based Dual phase Hardware Steganography for Securing IP cores", IEEE Letters of the Computer Society (LOCS) , 2019, Volume 2 , Issue 4, pp. 32-35
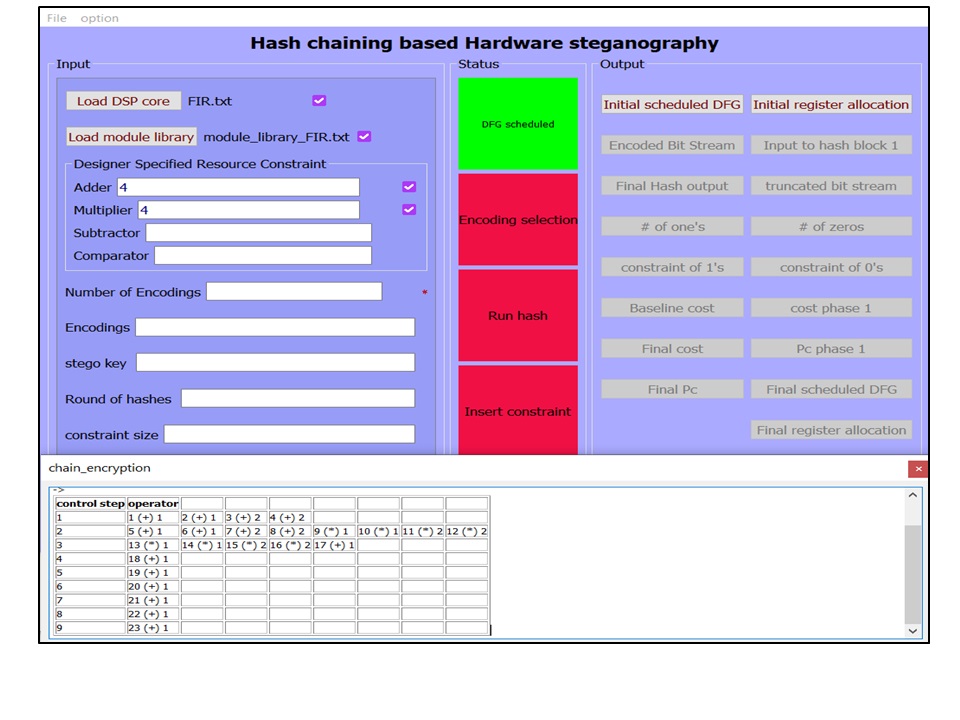
(6) KHC-Stego tool
-: Key-triggered Hash-chaining Driven Steganography tool
Click here to access the tool/Software in IEEE CEDA 'CAD for Assurance'
Click here for tool download
Click here to view the high-resolution tool GUI image
Summary and Threat Model : Dr. Sengupta and his team have developed a KHC-Stego tool to simulate and analyse the functionality of key-triggered hash-chaining driven steganography approach for securing DSP hardware accelerators against piracy and false claim of ownership threats.
Objective of the tool:The left portion of the tool shows the panel for providing required inputs to the tool, right portion shows the panel with output buttons to see the intermediate and final outputs of the key-triggered hash-chaining based steganography approach. The panel in the middle shows the status of the intermediate steps viz. CDFG scheduling of DSP application, encoding selection, executing hash-chaining process and insert constraints. Initially, these status bars remain red. Upon applying the inputs, the respective status bar turns green. The KHC-Stego tool accepts the DSP application input in the form CDFG along with module library and resource constraints. The tool shows output of intermediate steps of key-triggered hash-chaining based steganography, finally generated stego-constraints, the security metric in terms of probability of coincidence, pre and post-steganography design cost. Further, it also shows scheduling and registers allocation pre and post-embedding steganography constraints, onto the output window. The embedded steganography constraints in the hardware accelerator design can be used as digital evidence to secure against piracy and false claim of ownership threats.
Click here for accessing chapter 7 of the IET book on "Secured hardware accelerators for DSP and image processing applications" where details of the tool are provided
Supporting IEEE Publications:
- Anirban Sengupta, Mahendra Rathor "IP Core Steganography for Protecting DSP Kernels used in CE Systems", IEEE Transactions on Consumer Electronics (TCE) , Volume: 65 , Issue: 4 , Nov. 2019, pp. 506 - 515
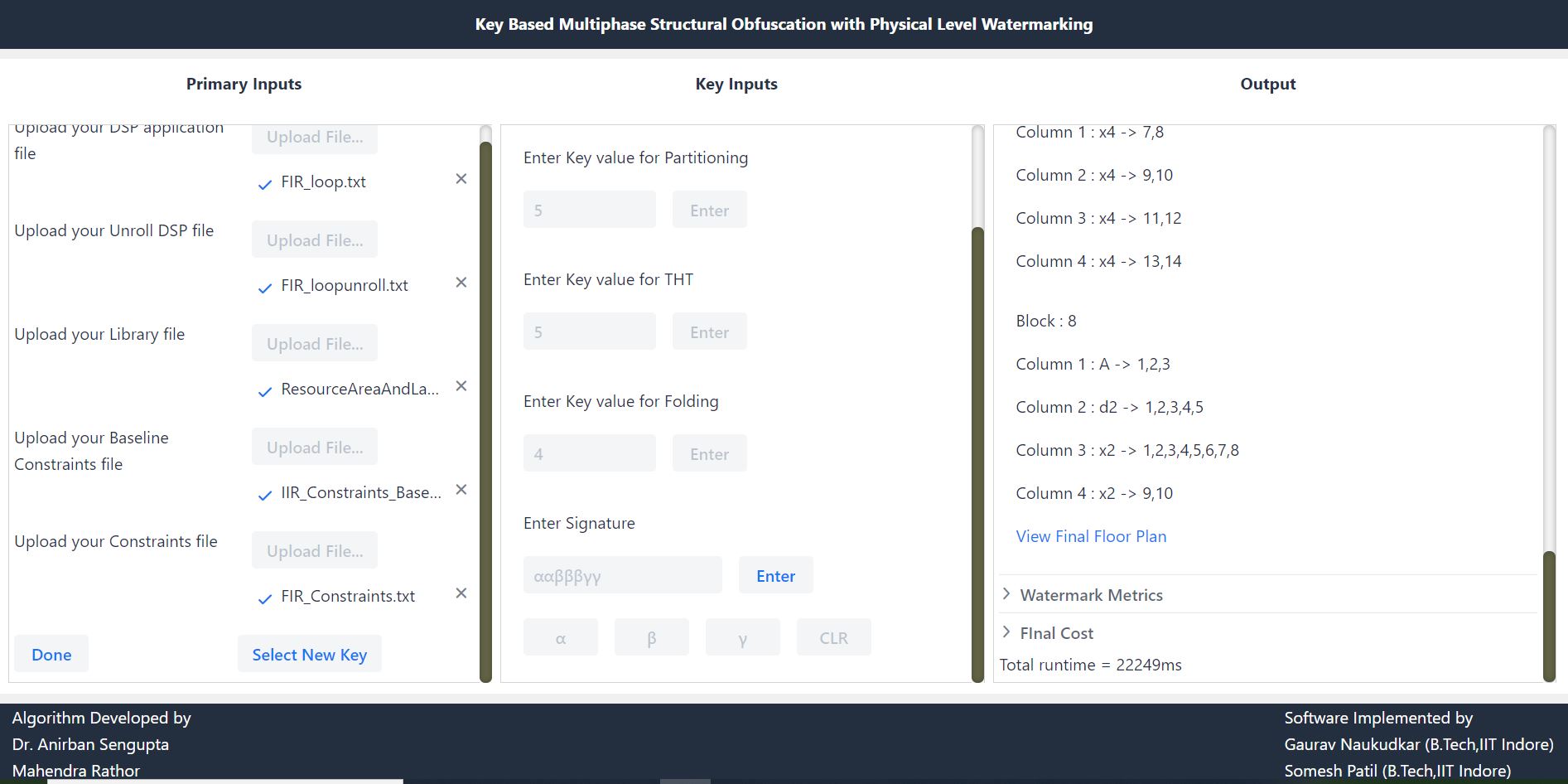
(7) KSO-PW tool
-: Key-driven structural obfuscation and physical level watermarking tool
Click here for tool download
Click here to view the high-resolution tool GUI image
Summary and Threat Model : Dr. Sengupta and his team have developed a KSO-PW tool to simulate and analyse the functionality of Key-driven structural obfuscation and physical level watermarking approach for securing DSP hardware accelerators against reverse engineering, piracy and false claim of ownership threats.
Objective of the tool: The left portion of the tool shows the panel for providing required inputs to the tool, right portion shows the panel with output buttons to see the intermediate and final outputs of the structural obfuscation and physical level watermarking based double line of defence approach. The panel in the middle shows the buttons for entering secret SO-keys (for multiple structural transformation techniques viz. loop unrolling, partitioning, ROE, THT and folding-knob) and vendor’s signature for watermarking. Since ROE is not applicable for FIR application, therefore the button for entering the ROE key input remains invisible. It is noteworthy in the GUI of KSO-PW tool that for a DSP application, only those secret key-buttons are activated for which the corresponding structural transformation techniques are applicable. The KSO-PW tool accepts the DSP application input in the form CDFG along with module library file and resource constraints file. The tool shows outputs of all intermediate steps of structural obfuscation and watermarking approach and finally generated watermarked floorplan of the obfuscated design. Further it also shows design cost before performing structural obfuscation and watermarking (i.e. baseline design cost), design cost after intermediate steps and the final design cost.
Click here for accessing chapter 4 of the IET book on "Secured hardware accelerators for DSP and image processing applications" where details of the tool are provided
Supporting IEEE Publications:
- Anirban Sengupta, Mahendra Rathor "Enhanced Security of DSP circuits using Multi-key based Structural Obfuscation and Physical-level Watermarking for Consumer Electronics systems", IEEE Transactions on Consumer Electronics (TCE) , Volume: 66, Issue:2, May 2020, pp. 163-172
- Anirban Sengupta, Mahendra Rathor, Somesh Patil, Naukudkar Gaurav Harishchandra "Securing Hardware Accelerators using Multi-Key based Structural Obfuscation", IEEE Letters of the Computer Society (LOCS) , Volume: 3, Issue:1, June 2020, pp. 21-24.
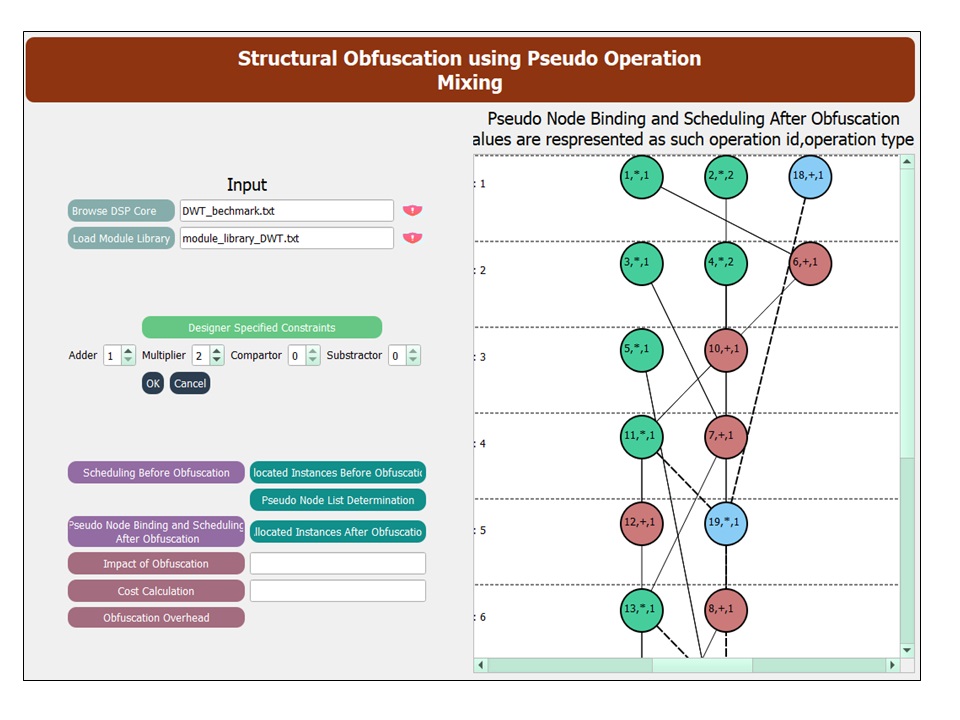
(8) POM-SO tool
-: Pseudo operation mixing based structural obfuscation tool
Click here for tool download
Click here to view the high-resolution tool GUI image
Summary and Threat Model : Dr. Sengupta and his team have developed a POM-SO tool (pseudo operation mixing based structural obfuscation tool) to simulate and analyse the pseudo operation mixing based obfuscation approach for securing DSP hardware accelerators against reverse engineering (and Trojan insertion).
Objective of the tool: The left portion of the tool shows the panel for providing required inputs to the tool and right portion shows the panel to see the intermediate and final outputs of the pseudo operation mixing based structural obfuscation approach. The POM-SO tool accepts the DSP application input in the form CDFG along with module library and resource constraints. The tool shows intermediate steps of pseudo operation mixing and finally generated structurally transformed scheduled and resource allocated DFG at the output. This output can be used to generate a structurally obfuscated RTL design of a DSP application which is un-obvious to an attacker and can hinder reverse engineering.
Click here for accessing chapter 9 of the IET book on "Secured hardware accelerators for DSP and image processing applications" where details of the tool are provided
Supporting IEEE Publications:
- Mahendra Rathor, Anirban Sengupta, "Obfuscating DSP Hardware Accelerators in CE Systems Using Pseudo Operations Mixing", IEEE International Conference on Zooming Innovation in Consumer Electronics 2020 (ZINC 2020) , Serbia, Accepted, May 2020